CVE-2025-56383 (Notepad++) — How to exploit DLL Proxying with CrimsonTools
CVE-2025-56383 is reported as a DLL hijacking issue in Notepad++ v8.8.3 where, under certain installation configurations, an attacker with local write access to the plugin directory can replace a legitimate DLL (in this case: NppExport.dll) with a malicious DLL. When Notepad++ loads that DLL at startup, the replacement can lead to arbitrary code execution on the host.
DLL Proxying - What is it ?
DLL proxying is the technique of replacing a legitimate dynamic-link library with a substitute DLL that exposes the same exports so the host application keeps working, while the proxy intercepts calls to run additional code. A proxy DLL typically performs its payload (for example in DllMain or in a specifically targeted exported function), then forwards the original call to the real implementation, often renamed and loaded dynamically, so the application’s expected behavior is preserved.
Analysis of NppExport.dll loading
To understand how this DLL might be abused, we begin by examining the functions that NppExport.dll exposes.
Start by launching Notepad++ and attaching x64dbg to the running Notepad++ process.
Once the debugger is attached, open the Symbols view, locate NppExport.dll, and take a careful look at the functions it exports.
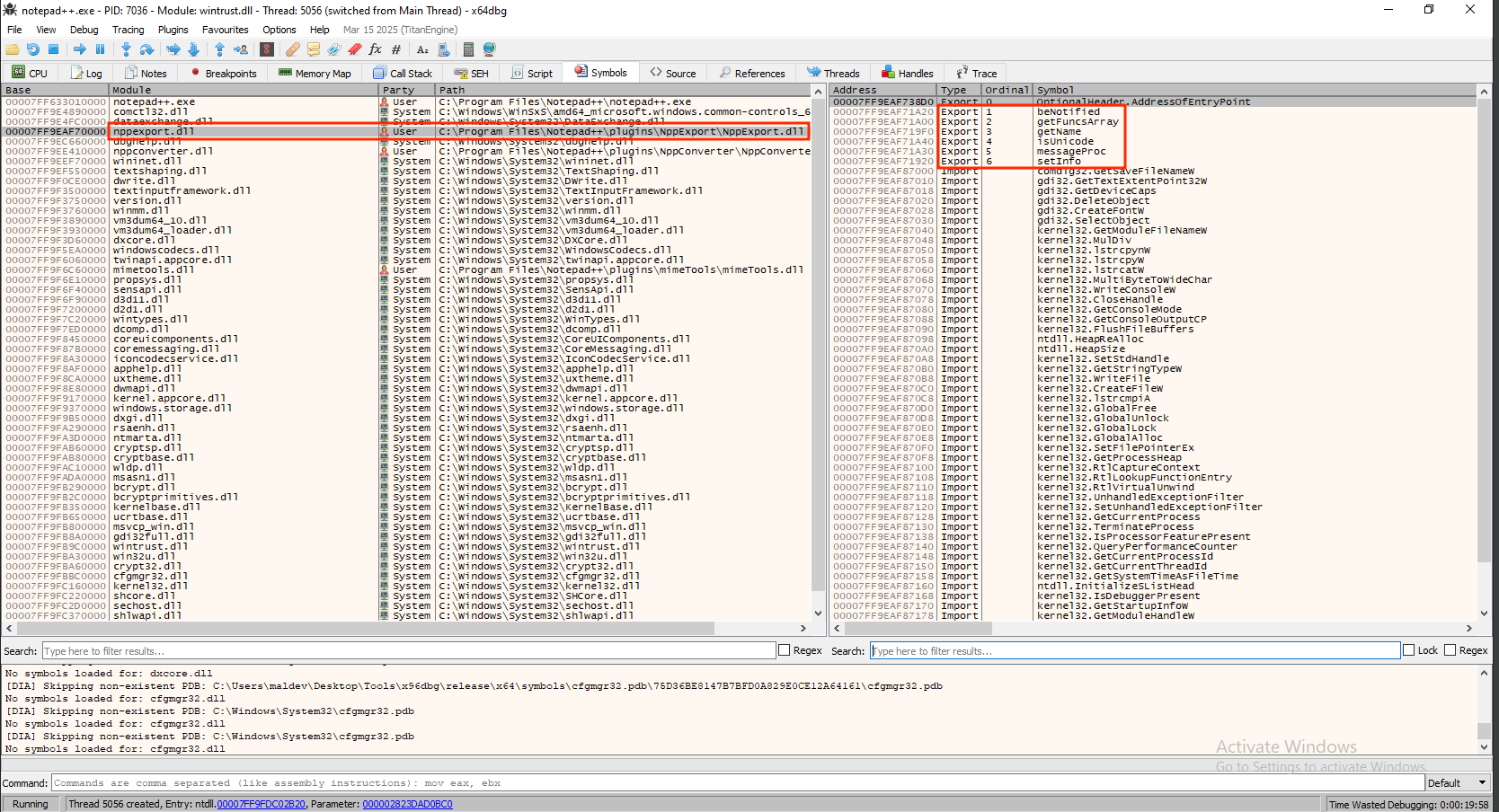
In this case, the exports listed for NppExport.dll are:
- beNotified (ordinal 1)
- getFuncsArray (ordinal 2)
- getName (ordinal 3)
- isUnicode (ordinal 4)
- messageProc (ordinal 5)
- setInfo (ordinal 6)
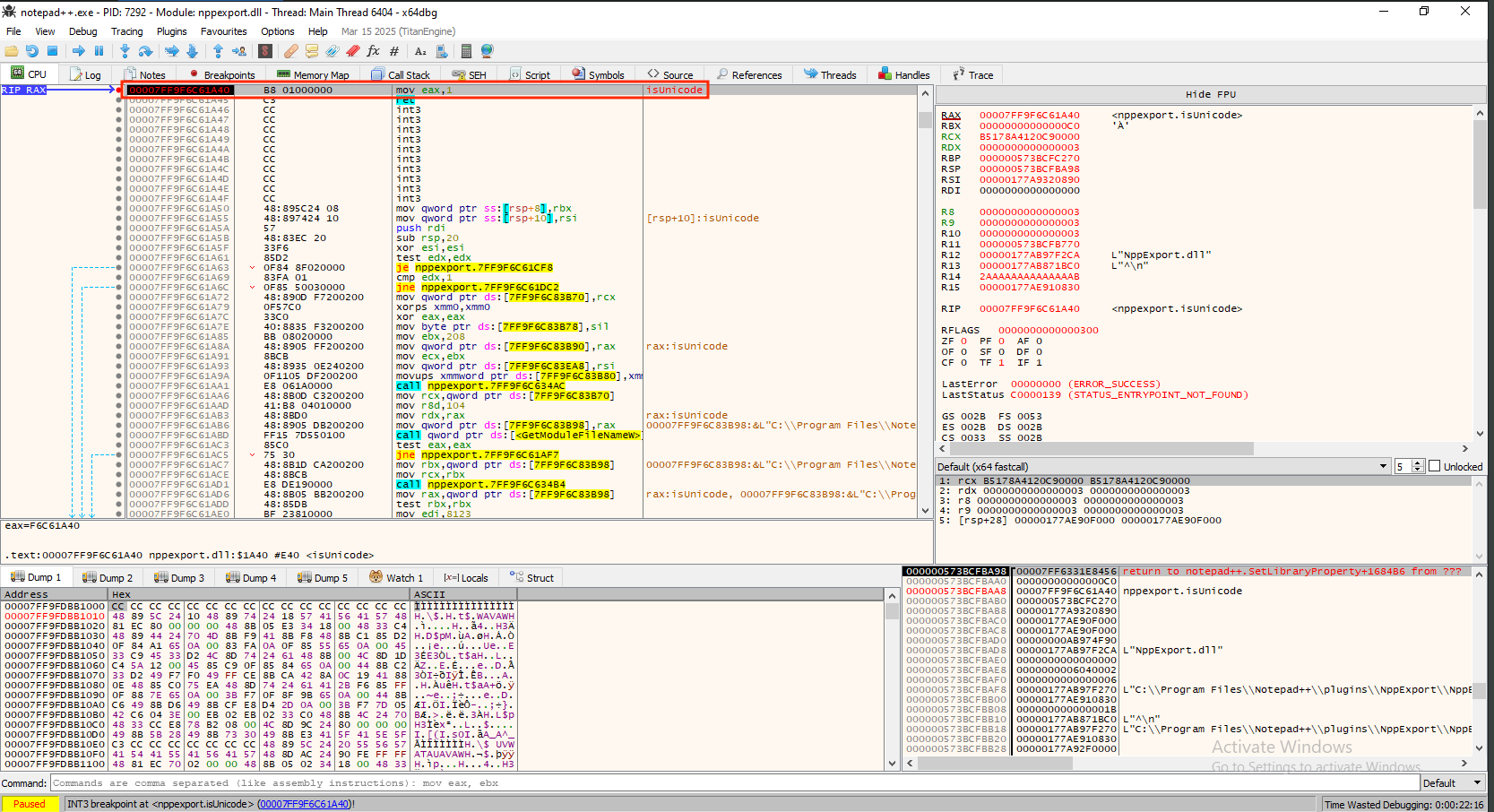
Knowing the names and ordinals is useful, but the key step is to verify which of these are actually invoked during the application’s lifecycle.
For this test, we set a breakpoint on isUnicode, relaunched Notepad++, and observed the breakpoint hit at startup — confirming that isUnicode is a valid and convenient target for our next phase, exploitation with CrimsonTools.
Exploitation with CrimsonTools
Now that we have identified an appropriate interception point, we use CrimsonTools to generate a proxy DLL that mirrors the exports of NppExport.dll and forwards calls to the original implementation.
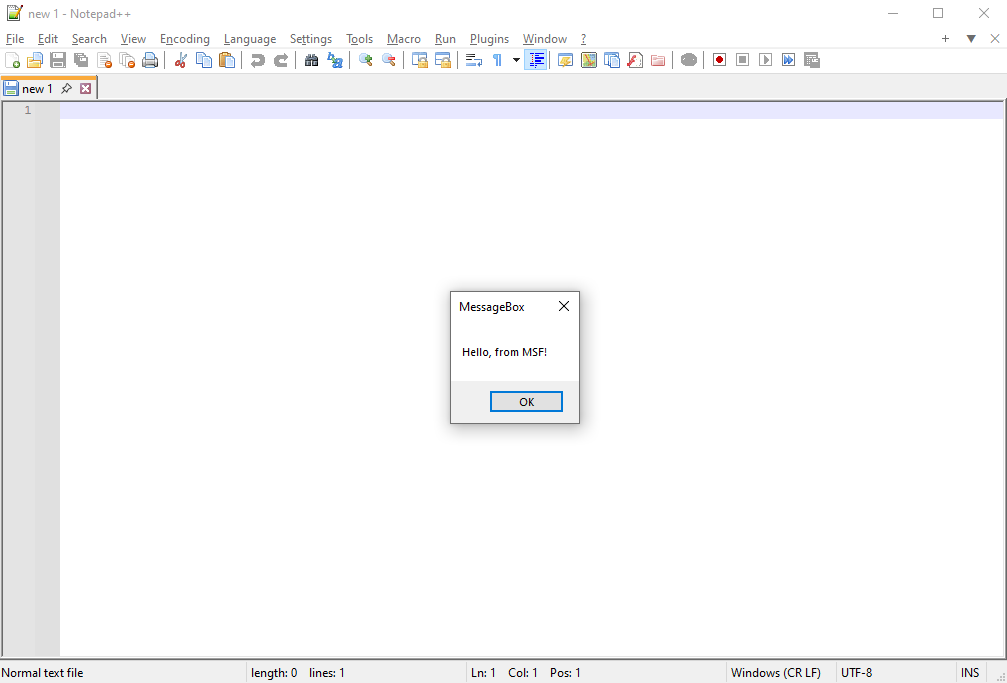
For this demonstration we use a simple MessageBox generated by msfvenom (this can obviously be replaced by shellcode generated by tools like Cobalt Strike, Sliver, Brute Ratel, etc.).
Next, we configure CrimsonTools for a proxy DLL output. In the CrimsonTools UI we select the DLL Proxy output format and fill the associated configuration fields according to the information previously gathered from our analysis.
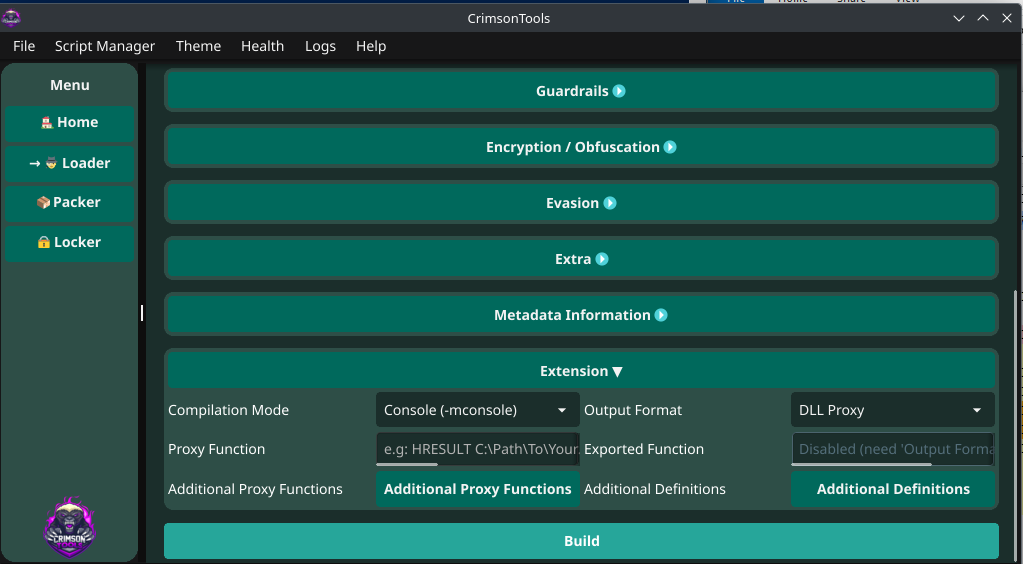
The function we target for this demonstration is isUnicode. In the CrimsonTools UI we indicate the primary function to proxy by specifying its return type, a reference to the original DLL, the function name and its ordinal, which gives us the following format for our case:
- VOID C:\Program Files\Notepad++\plugins\NppExport\NppExport_original.dll!isUnicode:4()
Before building, it is important to add support for the remaining exports to avoid unexpected behavior. In CrimsonTools these additional functions are configured via the Additional Proxy Functions option, where we must enter the names of the target functions, their ordinal numbers and the name of the original DLL.
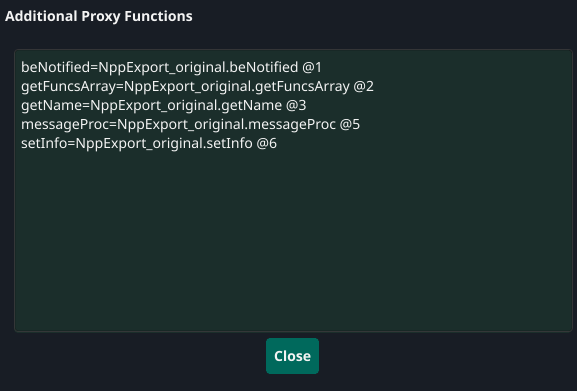
Once we have finished configuring our loader, we just need to press the build button, which will return our loader in .DLL format, ready to execute our shellcode.
After the build completes, we simply renamed the original DLL to NppExport_original.dll and replaced it with our loader.
All we need to do now is start Notepad++; upon launch, the shellcode executes successfully without affecting the host process!
Conclusion
This blog post shows how to use CrimsonTools to simplify payload generation, particularly for DLL proxying exploitation. A ready‑to‑use profile for this vulnerability (CVE-2025-56383) is available to customers.
Interested? Contact us to reserve a free 7‑day trial!