CrimsonTools
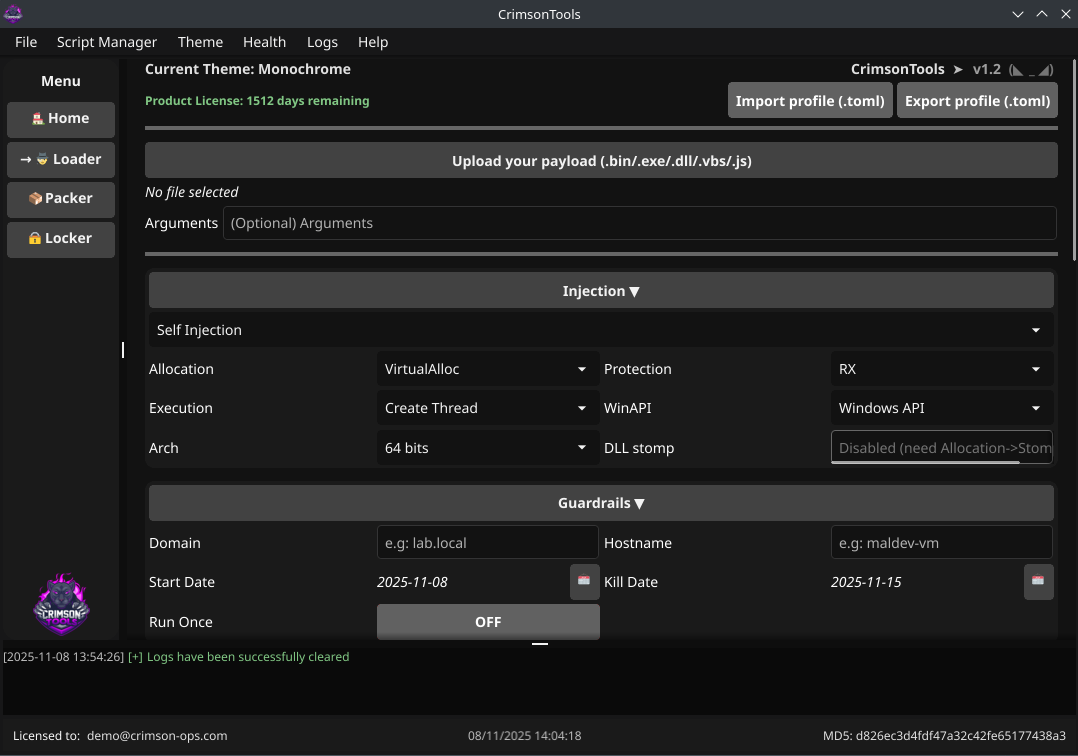
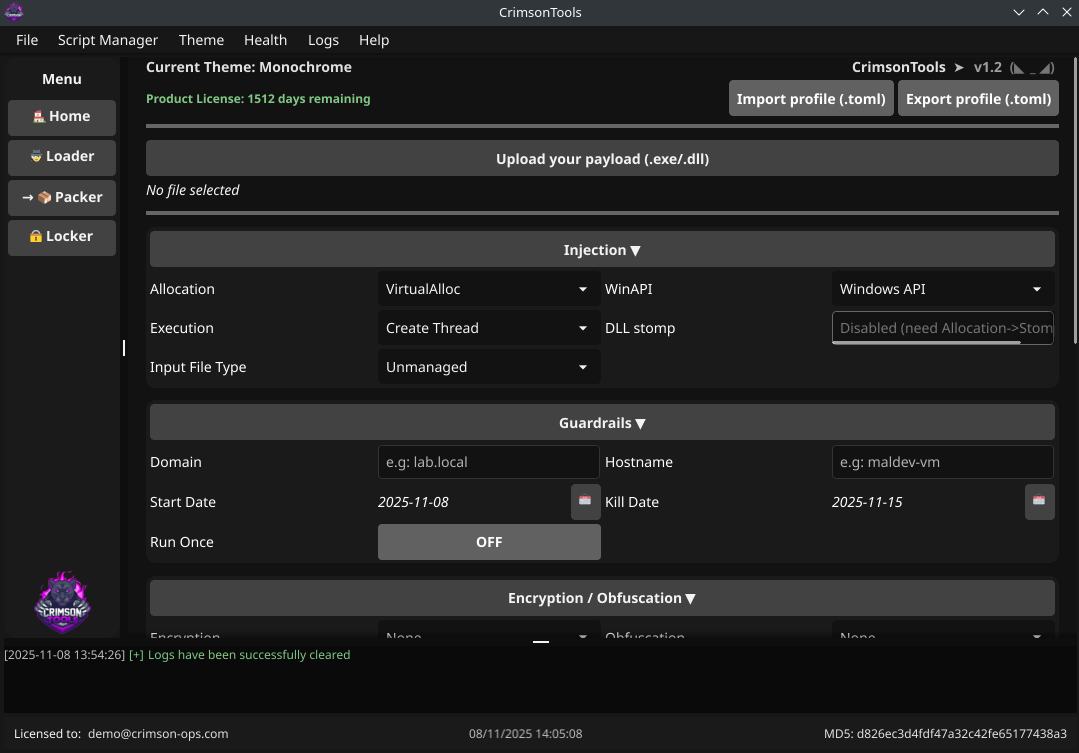
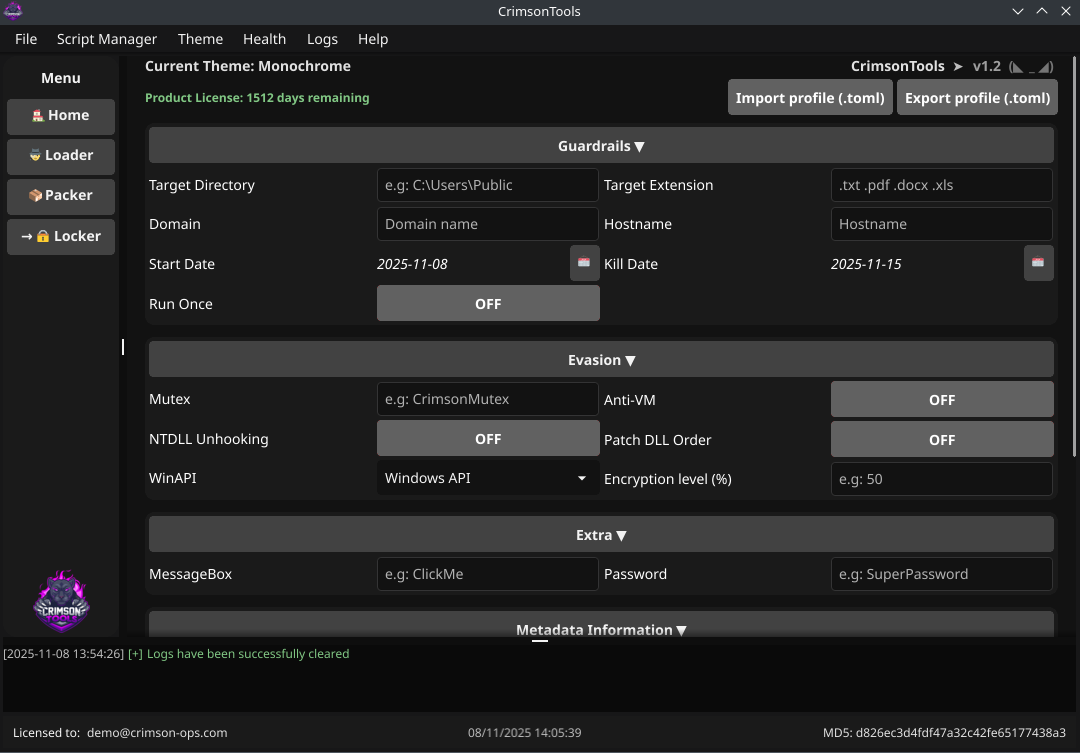
CrimsonTools is an advanced offensive security toolkit designed to help Ethical Hackers, Red Teams, and Purple Teams bypass modern antivirus and EDR solutions seamlessly. By automating and simplifying evasion techniques, it allows professionals to focus on actual exploitation and high‑value objectives rather than wasting time on complex security solutions bypassing.
Additionally, CrimsonTools includes a locker module that enables safe, controlled simulations of ransomware attacks to validate detection, response and recovery procedures.

Professional Grade Toolkit
Built for cybersecurity professionals who demand reliability, stealth, and effectiveness in their offensive operations.